Customer story
Hala Systems Deploys Verifiable AI Agents for OSINT
EQTY Lab and Hala Systems use AI agents to support European prosecutors in their mission to bring justice to Ukraine.
Key Takeaways:
Rapid, Trusted Insights: Hala uses AI agents underpinned with Verifiable Compute to rapidly transform overwhelming volumes of social media data, satellite imagery, and other publicly available information into actionable, tamperproof, linkage analysis, expediting casework that previously took months.
Transparency and Explainability: End-to-end auditability of this high-risk AI system ensures that all stakeholders—from judges interpreting complex evidence to engineers refining and expanding methodologies to compliance teams verifying standards—can confidently trust and fully understand the AI-driven process.
Regulatory Readiness: By building Verifiable Compute directly into its analysis workflows, Hala ensures its processes align with emerging AI regulations—such as the EU AI Act—preempting compliance challenges and protecting legal admissibility.
Secure, Resilient Infrastructure: A secure pipeline and layered trust architecture safeguard Hala’s systems against manipulation, ensuring critical records remain intact, defensible, and future-proof.
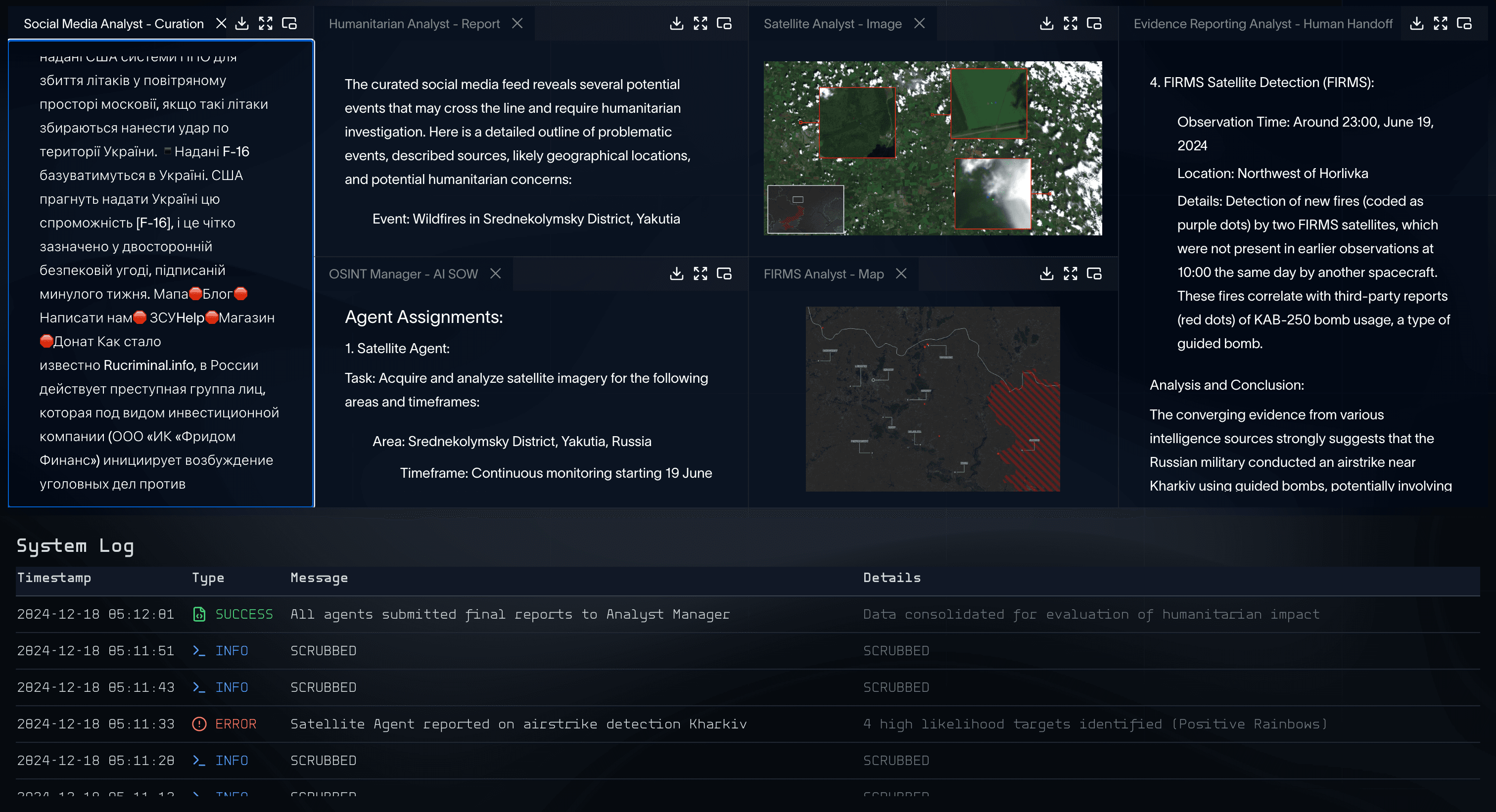
Over the last 18 months, Hala Systems and EQTY Lab have been working with the German Government as they seek accountability for war crimes in Ukraine in both domestic and international courts. The collaboration is enabled by a groundbreaking AI agent system capable of synthesizing vast troves of social media and satellite data into meaningful, court-ready analysis.
With a high-risk and critically important AI implementation, it’s not enough to simply deploy advanced systems—you must also prove that they can be trusted. EQTY has developed a tamperproof pipeline underwritten by Verifiable Compute on hardware-secured environments using Intel TDX and NVIDIA H100 GPU secure enclaves. The resilient certificates generated from Verifiable Compute, establish an auditable record of the governance of the data, models, and agents of the system.
This layered trust architecture ensures evidence is both protected against tampering and potentially admissible in legal proceedings, all while positioning organizations like Hala to meet new sovereign regulatory standards—such as those set out in the EU AI Act. The system protects critical infrastructure and sets the pace for trusted public sector AI strategies.
The Challenge
Russia's full-scale invasion of Ukraine is the most documented war in human history. Citizens, NGOs, and journalists use smartphones, drones, and commercially available satellite data to record a timely and detailed picture of the conflict. This form of publicly and commercially available data, referred to as open source intelligence, or OSINT, has augmented our understanding of the devastation and also surfaced clear and compelling potential evidence of war crimes.
To use OSINT in criminal investigations, prosecutors must be able to discern trustworthy and reliable information from the firehose of noisy data available online today. In addition, under the forthcoming EU AI Act Title III Article 6(2), AI systems used for investigative purposes by law enforcement qualify as high-risk and require the implementation of governance systems for risk management, documentation, oversight, accuracy, security, and transparency.
The Solution
To navigate the complex and real-time OSINT landscape, Hala uses AI agents to:
Aggregate information from social media platforms, such as Telegram.
Translate social media posts into English, using advanced translation models like those created by AppTek.
Identify incidents of interest based on the volume and accuracy of data.
Retrieve and fuse data with other complementary OSINT sources, such as satellite imagery.
Together, this critical analysis workflow must be secured with verifiable confidentiality and authenticity to achieve its maximal utility within investigations. For Hala to use AI agents for accountability, it first must hold its own agents accountable with clear governance.
The Technology
The nexus of verifiable and confidential activities is where Verifiable Compute brings transformational value. By using Verifiable Compute, cryptographic certificates are issued across AI agents and workflows, allowing investigators to collaborate and verify the provenance and confidentiality of OSINT data workflows and the corresponding analysis.
Hala deployed their series of AI agents within a Verifiable Compute environment. This provided the entire AI workflow and all insights and analysis with tamperproof cryptographic certificates detailing key information regarding both the hardware and software deployed at the time of the process. In addition to securing and sealing evidence, cryptography can also help ensure sensitive data is protected and encrypted as needed and enable permissioned systems, meaning data is only available to those with the appropriate access.
These cryptographic proofs establish a next-generation chain of evidence that enables third parties to validate and verify the authenticity, provenance, and integrity of the data and the agents that are provisioned to assist. This level of granularity on an AI system is unprecedented in the international legal and humanitarian fields.
What is Verified
Hala’s agentic system’s strength lies in its ability to scale the governance of its semi-autonomous workflows. Using EQTY’s framework, AI development can become more innovative as it becomes more verifiable.
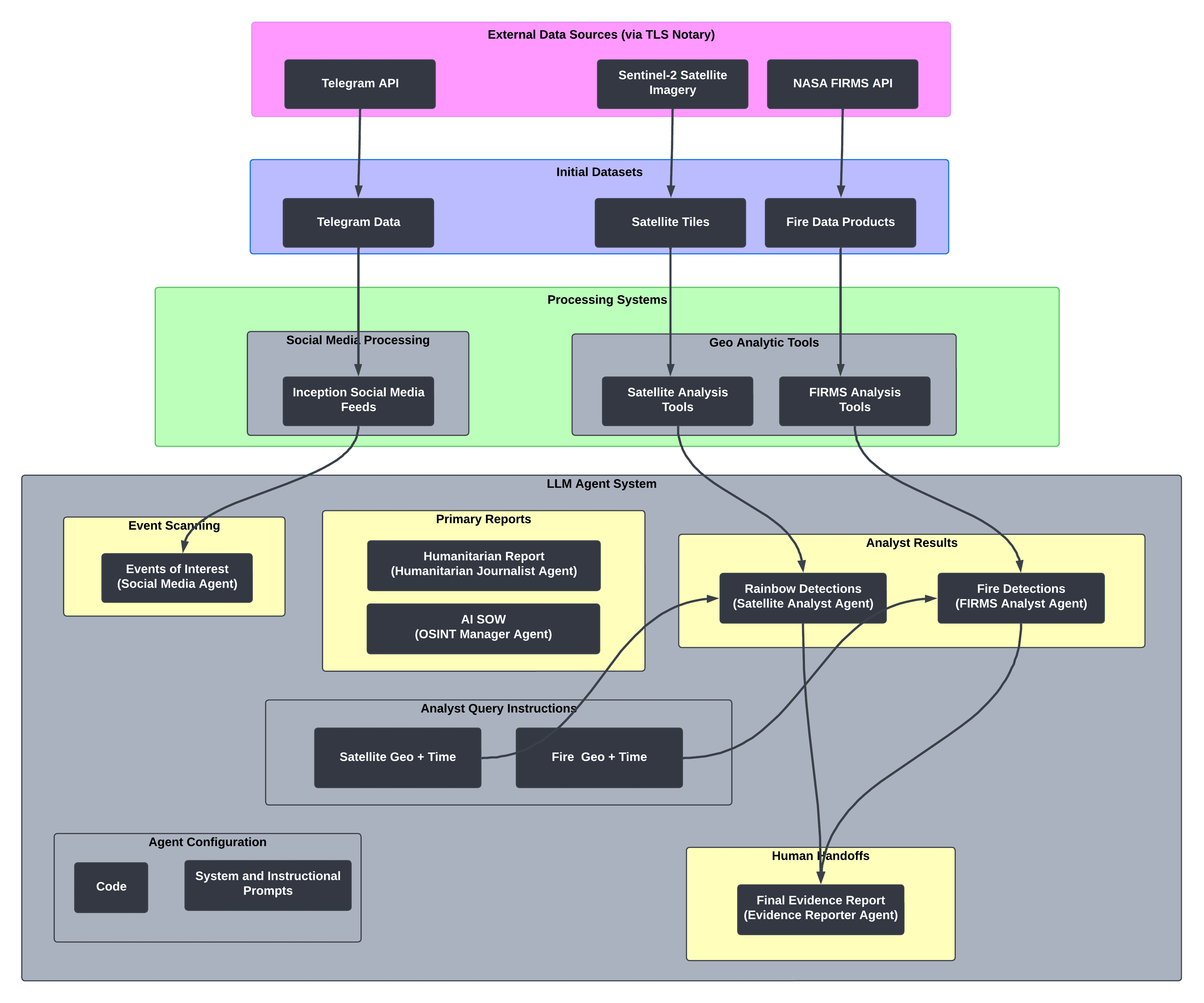
Data: Verification begins with data collection from Telegram messages, Sentinel satellite imagery, and NASA's fire detection system (FIRMS). Each data source is verified through a TLS notary, creating cryptographic attestations that prove the authenticity and timing of every piece of information collected. This verification extends to the data ingestion process, with continuous checks ensuring data integrity throughout updates.
Code: AI agents' configuration and analytical tools are verified before execution. The notary proves what data was analyzed and how it was processed and then continuously notarizes the agent activity.
Agents: A network of specialized AI Agents conducts the autonomous analysis. These specialized agents include:
Social Media Agent: This agent processes Telegram posts in a verified database aggregated by Hala Systems. The agent retrieves the most recent information, which is automatically translated using a verified AppTek's Translation Model.
Humanitarian Journalist: The translated findings flow into this agent that develops initial investigative reports.
OSINT Manager: This agent creates structured query instructions for specialized analyst agents focusing on satellite imagery and FIRMS data. The OSINT Manager creates an “AI SOW” with the included instructions for analysis (i.e., Geolocations to query, time spans, etc.). The structured instructions are passed to each respective analyst agent.
Specialized Analyst Agents: AI analyst agents use dedicated analytical tools to process their respective data sources – all within the verified environment. Each analytical step maintains the chain of verification, with external services called during analysis verified through a TLS notary. A Satellite Detection Analyst searches for specific patterns in imagery. A FIRMS Analyst looks for and correlates fire detection data.
Evidence Agent: When meaningful correlations are found, this agent compiles a comprehensive report for human analysts to review. Importantly, this final step only occurs when the system detects significant, corroborated events – creating a powerful filtering mechanism for continuous OSINT monitoring that only surfaces the most relevant incidents for human investigation.
Future-proofing for Tomorrow’s AI Standards
The system's true power lies in this unbroken chain of verification from source to analysis. When evidence is compiled for court, investigators can prove with Verifiable Compute certificates the authenticity of every data point, the integrity of every computation – including language translations – and the validity of every analytical step. This level of verification transforms digital evidence from questionable data into court-admissible documentation that can withstand rigorous legal scrutiny. They must also be resilient over time, keeping their integrity over the decades it takes for accountability to conclude.
For human rights organizations and international courts, this represents a crucial advancement. The combination of continuous AI processing and expert human review, backed by complete computational verification, allows for a faster, more thorough investigation of potential war crimes while maintaining the highest standards of data integrity.
In summary, Verifiable Compute provides proof of:
A chain of evidence needed for the judiciary to trust the data and have a clear and explainable algorithmic audit to ensure all governance around it has been followed.
Privacy protection ensuring that sensitive data can be aggregated from multiple sources across several jurisdictions while preserving the intent, scope, and governance needed to comply with privacy regulations.
Auditable compliance with regulations, proving AI investigations deploy safeguards to comply with applicable local and international laws, including international humanitarian law.
Human and ethical oversight through attestations from supervisors that ethical assessments and end-user feedback ensure human oversight mitigates any unintended harm and/or harm resulting from the unintentional bias of the technology.
Looking Forward
Hala Systems and EQTY Lab will continue to jointly pursue opportunities to further the frontier of use cases where organizations and enterprises must carry out complex tasks with immense amounts of information thoughtfully and responsibly and in turn, be able to prove that they did. In addition to national security and human safety, Verifiable Compute increases resiliency across sectors.
About Hala Systems
Hala Systems is a pioneer of AI-driven multi-modal intelligence fusion leveraging OSINT across multiple missions. Hala specializes in developing advanced technology solutions for situational awareness, accountability, and protection. The company offers unclassified remote sensing and alerting systems that leverage artificial intelligence (AI) and the Internet of Things (IoT) to provide actionable intelligence and early warnings. These systems are designed to predict, prevent, and respond to threats, thereby increasing resilience and security.